Call Us
Mail Us For Support
Office Address
208, Suratwala Mark Plazo,
Pune, India-411057
Pune, India-411057
Now Hiring: Are you creative, self driven and motivated Developer?
Office Hours: 10:00am-7:00pm
Office Address
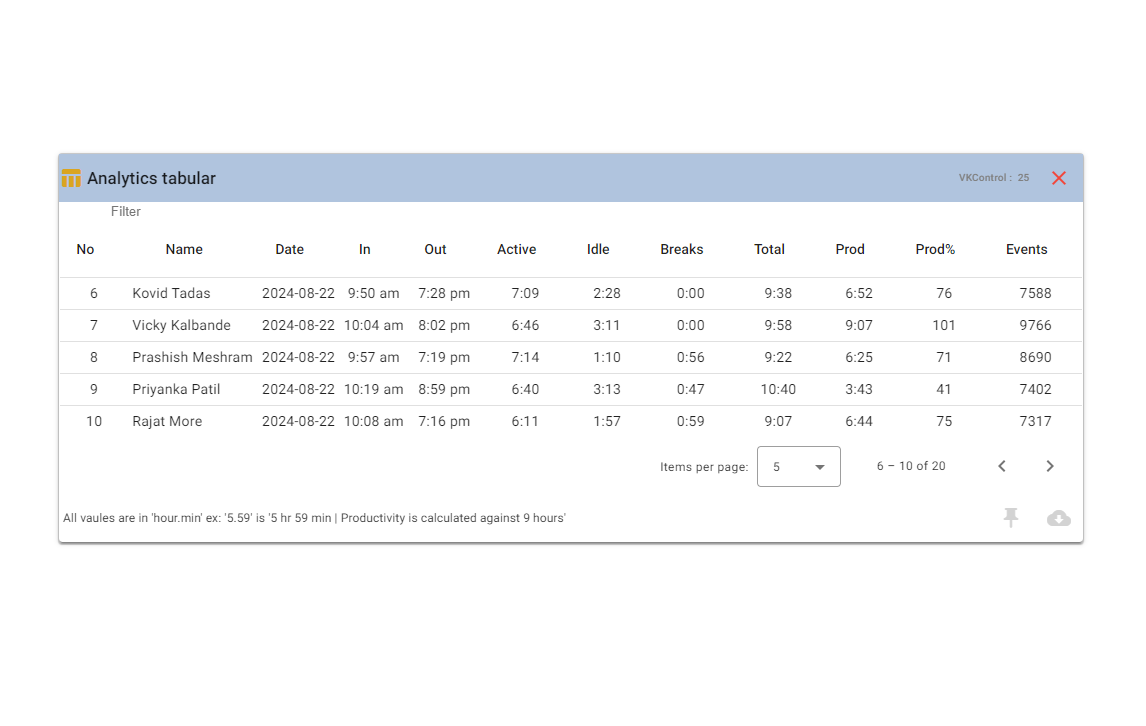
Keystrokes and mouse click counting software helpful to the organization to measure the employees working activeness during working hours. When the Tabular Analytics report exported and open in excel, we found the "Event" column. The values of event columns show the sum of the keypresses and mouse clicks for each employee. While analyzing the tabular analytics reports the event column values of each employee defines the most and least activeness while working.
Active employees are not all time working on the productive stuff while analyzing the data of event column in tabular reports the most active and least active employee can find out easily. In specific industries, this is very important to measure the work done by the employee..
Track each employee’s keypress events for insights into productivity and engagement.
Measure combined keypresses and mouse clicks to determine overall activity levels.
Identify consistently active and inactive employees for better performance assessment.
Highlight the best-performing employee based on consistent activity metrics.
Focus on improving the least active employees through targeted strategies.

Attention! Attention!! Attention!!!
While analyst analyzes the organization employee data, there are multiple factors considerations to know how the organization performs. The performance of the organization is fully dependent on the there employees working. Employees working over the working hours are very difficult task to measure the actual work. Not 100% but more than 70% in some industries and more than 90% in specific industries the count of keypresses and mouse clicks define the productivity. This event varies from team to team and from the analysis of the tabular data it is found out. This helps organizations for improvement in the specific department and take action for over productivity improvement.

Per Month Per Employee Charged Annually
$2 / per month
Get StartedIncludes Plan :
Per Month Per Employee Charged Annually
$5 / per month
get startedIncludes Plan :
Per Month Per Employee Charged Annually
$8 / per month
get startedIncludes Plan :
Data security is a crucial aspect of modern age society as more and more personal and sensitive information is stored and processed online way, Here keeps in mind that encrypting sensitive data makes it unreadable to anyone without a proper decryption key is not generated. This is very important for the information transmitted such as when sending emails or using online other websites for work. And, for banking transactions. Keeping strict access control in the office URLs and servers such as two-factor authentication can help to prevent unauthorized access during working hours.
We give a regular backing up feature that your data ensures that you can restore it in the event of data loss or data corruption or during the time of power cut. Limit access to those who needed or give privileged access to authorized employees of your business or organization. You can also store backups in a secure location such as an external hard drive which is very easy to connect and fast to transfer the data and also portable you will also store it in cloud-based storage. Keep physical devices such as laptops and hard drives locked up and log out when not in use it stores sensitive information in a secure location.
Regular updates to your software and operating system can help to prevent security vulnerabilities and less the risk to hack your systems and organization assets. Keep a watch or eye out for security patches and updates from the new versions of software releases. Monitoring your systems for potential security threats and having a plan in place for responding to incidents can help to prevent data loopholes and phishing. Your employees are often the first line of defense when it comes to data security Train them to be aware of the potential threats and to follow the best practices for data security. Properly disposing of the data when no longer needed is essential for protecting sensitive information Wipe drives and devices before disposing of them to ensure that cannot be recovered.
For organizations and offices, we recommend trying our On-premises Solution. Enterprises also apply their Security of Employee Information own data security policies for the on-premises and get ensure your all data will be secure also taking a multi-layer approach and being proactive to implement the best we can help protect your sensitive information and prevent loopholes in the security. When employees attain a state of sanctification, they go beyond mere contentment with their work; it transforms into a sense of calling and dedication. Their work transcends being just a job; it evolves into a vocation. They approach their tasks with a profound sense of purpose and unwavering commitment that extends beyond the material aspects of employment.
Employee sanctification frequently results in elevated levels of engagement, loyalty, and enduring dedication to an organization. It harmonizes closely with an employee's values and convictions, forging a deep and meaningful connection between the individual and their work.
In conclusion, employee satisfaction forms the foundation for the broader concept of employee sanctification. When employees find satisfaction in their work environment, receive recognition, and have access to growth opportunities, they are more likely to discover sanctification in their roles. This sense of sanctification can lead to heightened commitment, increased productivity, and a profound sense of fulfilment, benefiting both employees and their organizations.
Demo helps to know overall available features and our unique design of the user interface as we have "Work-Board" instead of dashboard to avoid the complexity during the accessing the software.